Legato's runtime architecture manages each app in its own sandbox.
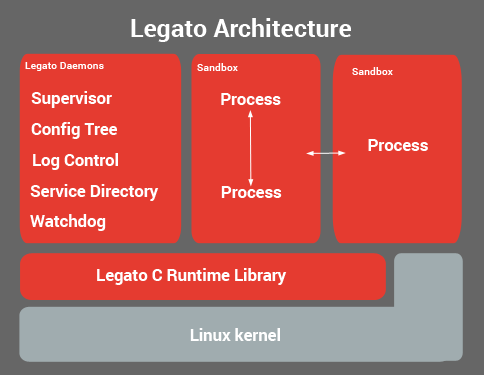
Apps communicate with each other using access-controlled message-passing services.
The Supervisor automatically creates sandboxes.
An application (we call them 'apps') is a collection of executable files, libraries, and/or other resource files (e.g., audio files, web pages) that can be deployed to a target device. Once installed on a device, an app can be started and stopped.
By default, each app runs in its own sandbox. When an app is constructed, all the files and IPC services it needs to access are declared. At runtime, the Supervisor and the Service Directory enforce that only approved files and IPC services are accessed by that app.
The Supervisor is a privileged process running on the target device that:
Legato's Service Directory provides a secure way for client processes to find servers offering services they need, which ensures only authorized connections are established.
The Config Tree provides persistent Configuration data storage organized in a tree structure.
Command line config tool
Config Tree API
Legato kickable watchdog service provides a timeout that can be configured in defFilesAdef or specified at run time. If a kick is not received in the specified time, the supervisor signals to perform the action specified in Watchdog Action.
Watchdog Service
Application Definition .adef
Legato provides a user-friendly way to control log message filtering for running app processes.
Command line log tool
Logging API.
The Update Daemon accepts "update pack" files, which contain software/firmware update instructions and associated data, such as libraries, executables, and resource files.
Update packs can be fed to the Update Daemon via the Sofware Update API or through the toolsTarget_update tool.
The Update Daemon includes hooks that allow update packs to be digitally signed and/or encrypted for security reasons.
Copyright (C) Sierra Wireless Inc. Use of this work is subject to license.